AWS ALB to Lambda
code for article pfeilbr/aws-alb-to-lambda-playground
learn ALB to Lambda integration
Notes
- AWS provided DNSName for the ALB is of the format
xxxxxxx.us-east-1.elb.amazonaws.com - the ALB DNSName does not provide SSL termination by default
- you cannot request a certificate for the ALB DNSName (
xxxxxxx.us-east-1.elb.amazonaws.com) via ACM - if you own the domain, you can request a certificate (e.g.
alb01.allthecloudbits.com) via ACM and have it automatically validated via route 53 CNAME record (see DomainValidationOptions )In order for a AWS::CertificateManager::Certificate to be provisioned and validated in CloudFormation automatically, the
DomainNameproperty needs to be identical to one of theDomainNameproperty supplied in DomainValidationOptions, if the ValidationMethod is DNS. Failing to keep them like-for-like will result in failure to create the domain validation records in Route53. - you can specify a single certificate for your
AWS::ElasticLoadBalancingV2::Listenervia theAWS::ElasticLoadBalancingV2::Listener Certificateproperty. If you need multipe certificates, useAWS::ElasticLoadBalancingV2::ListenerCertificate
Demo
based on alexcasalboni/template.yml - AWS ALB - AWS Lambda integration with CloudFormation (YAML) includes a custom domain name CNAME’d to the ALB hostname with ACM cert for https
lambda function code is inlined in template.yaml
# deploy stack
sam deploy
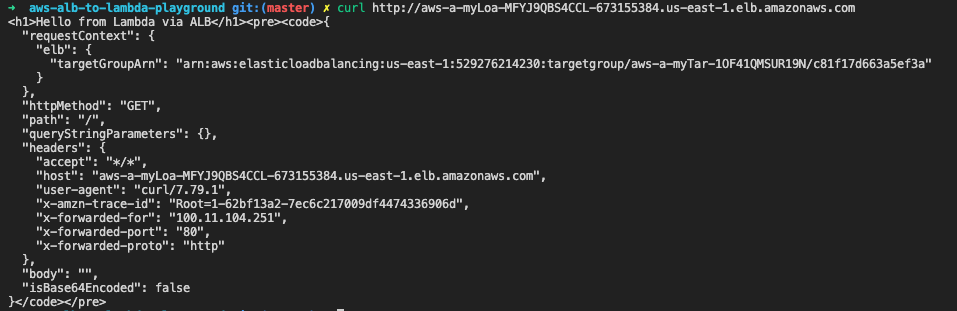
# check our ALB andpoint
curl http://aws-a-myLoa-MFYJ9QBS4CCL-673155384.us-east-1.elb.amazonaws.com
# output:
# <h1>Hello from Lambda via ALB</h1><pre><code>{
# "requestContext": {
# "elb": {
# "targetGroupArn": "arn:aws:elasticloadbalancing:us-east-1:529276214230:targetgroup/aws-a-myTar-1OF41QMSUR19N/c81f17d663a5ef3a"
# }
# },
# "httpMethod": "GET",
# "path": "/",
# "queryStringParameters": {},
# "headers": {
# "accept": "*/*",
# "host": "aws-a-myLoa-MFYJ9QBS4CCL-673155384.us-east-1.elb.amazonaws.com",
# "user-agent": "curl/7.79.1",
# "x-amzn-trace-id": "Root=1-62bf13a2-7ec6c217009df4474336906d",
# "x-forwarded-for": "100.11.104.251",
# "x-forwarded-port": "80",
# "x-forwarded-proto": "http"
# },
# "body": "",
# "isBase64Encoded": false
# }</code></pre>
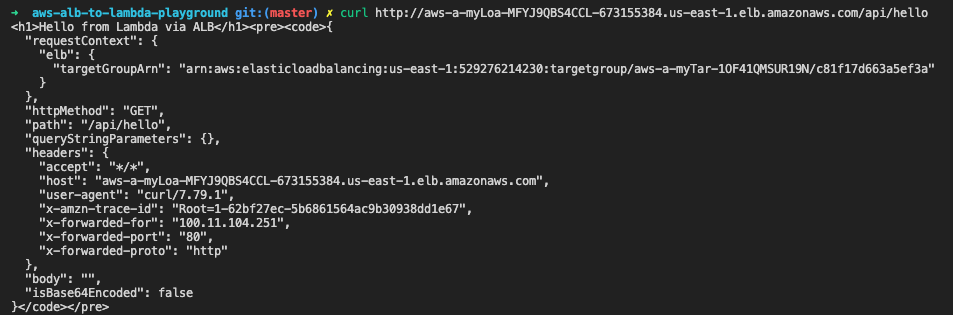
# check path based listener (`/api/*`)
curl http://aws-a-myLoa-MFYJ9QBS4CCL-673155384.us-east-1.elb.amazonaws.com/api/hello
# output:
# <h1>Hello from Lambda via ALB</h1><pre><code>{
# "requestContext": {
# "elb": {
# "targetGroupArn": "arn:aws:elasticloadbalancing:us-east-1:529276214230:targetgroup/aws-a-myTar-1OF41QMSUR19N/c81f17d663a5ef3a"
# }
# },
# "httpMethod": "GET",
# "path": "/api/hello",
# "queryStringParameters": {},
# "headers": {
# "accept": "*/*",
# "host": "aws-a-myLoa-MFYJ9QBS4CCL-673155384.us-east-1.elb.amazonaws.com",
# "user-agent": "curl/7.79.1",
# "x-amzn-trace-id": "Root=1-62bf27ec-5b6861564ac9b30938dd1e67",
# "x-forwarded-for": "100.11.104.251",
# "x-forwarded-port": "80",
# "x-forwarded-proto": "http"
# },
# "body": "",
# "isBase64Encoded": false
# }</code></pre>
# check our custom domain
curl http://alb01.allthecloudbits.com
# check our custom domain https endpoint
curl https://alb01.allthecloudbits.com
# clean up
sam delete --no-prompts
Resources
- alexcasalboni/template.yml - AWS ALB - AWS Lambda integration with CloudFormation (YAML)
- Lambda functions as targets for Application Load Balancers
- Application Load Balancer can now Invoke Lambda Functions to Serve HTTP(S) Requests
- One Load Balancer to rule them all
- How do I associate multiple ACM SSL or TLS certificates with Application Load Balancer using CloudFormation?
- AWS::ElasticLoadBalancingV2::LoadBalancer
- AWS::ElasticLoadBalancingV2::Listener
- AWS::ElasticLoadBalancingV2::ListenerCertificate
- AWS::ElasticLoadBalancingV2::ListenerRule
- AWS::ElasticLoadBalancingV2::TargetGroup